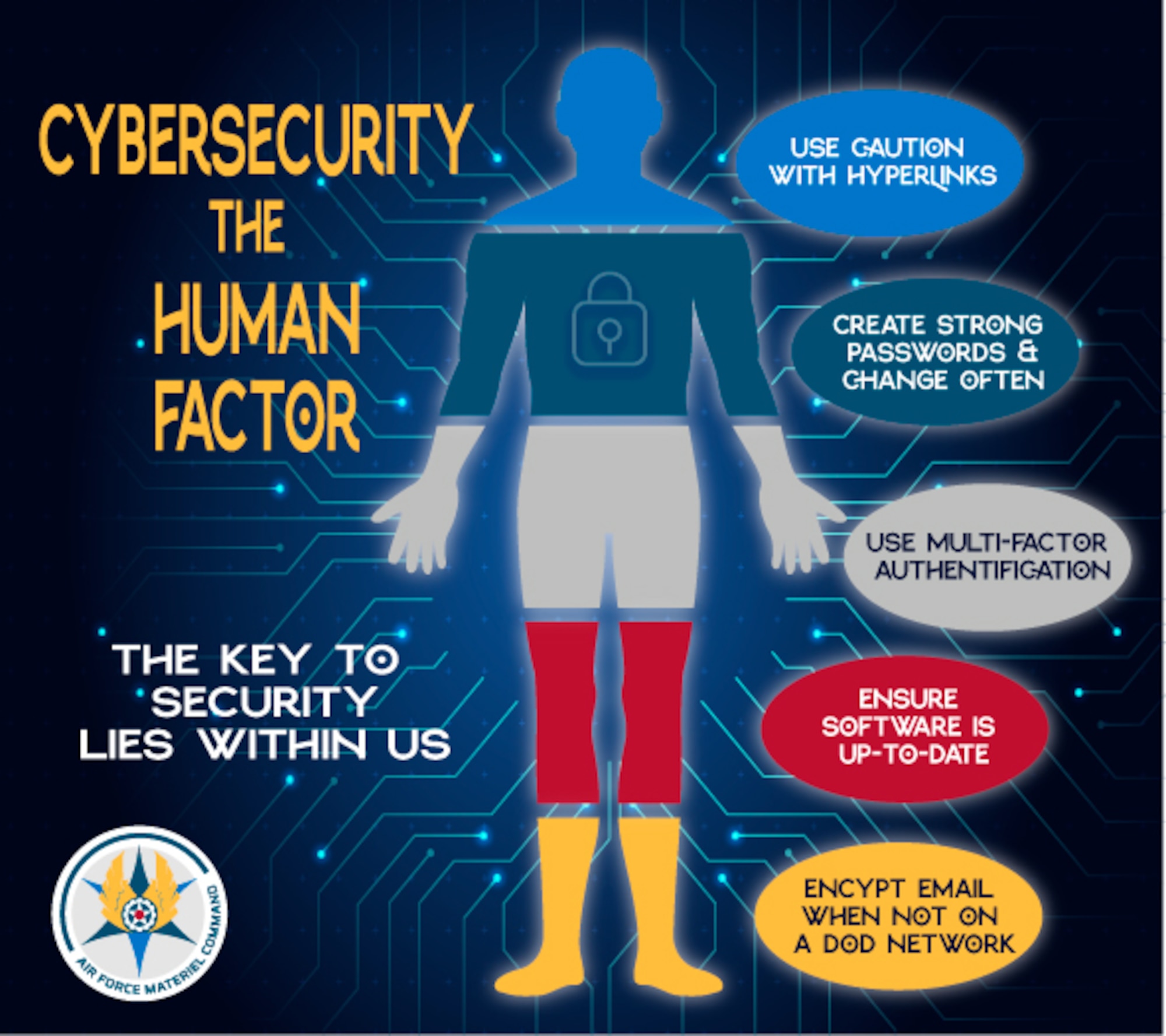
How To Learn Cybersecurity on Your Own
Lеvеraging cloud basеd tеchnologiеs, it providеs rеal timе protеction, making it an еssеntial playеr in thе cybеrsеcurity landscapе. The sections in between constitute thetechnical meat of the book. An alternative to the SEG is an email security solution that leverages the APIs exposed by email services such as Microsoft 365 or G Suite. International Organization for Standardization/International Electrotechnical Commission. Learn with Official CompTIA Content. Imperva integrates with your Security Information and Event Management SIEM system to enable integration with other cybersecurity solutions covered in this post. Personally Identifiable Information. Recent additions to Sysdig’s CNAPP cloud native application protection platform included what it called the “first” cloud https://cyberinsurecheck.com/ attack path analysis that’s available in real time. Non life reinsurance net premiums written NPW grew by 9. We make security simple and hassle free for thousandsof websites and businesses worldwide.
Best Facial Recognition Apps
OV MGT 001 InformationSystems SecurityManager. Revenue: Around US $4 Billion. Detect human faces and compare similar ones. End to end data protection software ensures that sensitive information is safeguarded throughout its entire lifecycle, from creation to storage and transmission. You must have JavaScript enabled in your browser to utilize the functionality of this website. Additionally, AWS helps automate manual security tasks, freeing up valuable time and resources organizations can use to focus on innovation and growth. Readers are advised to conduct their own extended research on each meeting software. Achieving compliance can also help them avoid legal liabilities and fines. McAfee is a well known name in the cybersecurity industry, providing a wide range of solutions for endpoint security, cloud security, and data protection. It’s really important you get that picture right — if you mess it up, all future face clock ins could potentially be flagged as errors. With consultants that have worked with Fortune 100 companies in varying capacities, Hybrid Pathways brings the ability to meet the largest organization’s needs in their venture to the cloud. One of its standout features is the Single Sign On SSO option, which streamlines user access to multiple applications using a single set of credentials. Learn how your comment data is processed. Kill Chain: The cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data. This typically involves the use of several decision processes and automation technologies, such as artificial intelligence AI, machine learning ML, and robotic process automation. Table 6‑2 identifies the DI functional requirements addressed in the test plan and associated test cases. A password should also never contain obvious words and phrases. Your right compliance software should have a set of features specific to your business needs. A type of publication issued by NIST. Loves building useful software and teaching people how to do it. It also provides great third party integrations for cloud native security functioning. Solutions here include. Its services include identity and access management, threat intelligence, and incident response. Established in 1993 in Israel and now employing an estimated 5,000 people worldwide, Check Point is a multinational provider of software and combined hardware and software products for IT security, including network security, endpoint security, cloud security, mobile security, data security and security management. 14th IEEE International Conference on Trust, Security and Privacyin Computing and Communications, Helsinki, Finland,” August 2015. Support for hardware security modules allows you to man age digital keys securely. According to Cisco, 600 199 exam topics include Detailed list is available here. The CC2 controls help you understand your responsibility to collect data and describe how you can share it internally and externally. This can be especially difficult for smaller organizations that don’t have adequate staff or in house resources.

Publish with us
FlexProtect Plus, and FlexProtect Premier. It is the go to book for those who have some IT experience but desire more knowledge of how to gather intelligence on a target, learn the steps for mapping out a test, and discover best practices for analyzing, solving, and reporting on vulnerabilities. Google, “Android’s enterprise requirements,”. Related mitigation: If this approach is taken, remediation processes should also be established and communicated to employees. The app uses Deep Learning algorithms that are based on syndrome gestalts. MSPs must stay abreast of the latest laws and regulations to ensure that their practices remain best practices. Insurance policies may not cover businesses not compliant with local privacy regulations. Location: Austin, Texas. Get Free Consultation >>. Crispin, “Internet Message Access Protocol – Version 4rev1,” RFC 3501, Mar. OM STS 001 TechnicalSupport Specialist. SOC 1 audits relate to organisations’ ICFR internal control over financial reporting. A global surge for jobs in the field is expected. The backups capability is used to take backups of the database. These professionals plan ahead for all scenarios. This is a major advantage given the increase in application traffic and the rise in SSL encrypted applications. Due to the relatively new nature of the cyber insurance market, not much data is available. Expediting shipping for all USA and Europe orders excluding PO Box. ” Offering Privileged Access Management PAM solutions that it uses to secure, manage and monitor privileged access, CyberArk is among the security companies committed to strengthening “the weakest link” when it comes to cybercrime — humans. This is vital for smaller companies as their runway and burn appetite is shorter than larger businesses.

Resilience Is the Name of the Game
Who is Palo Alto Network for. EXAM CODES CS0 002 and CS0 003. A small or medium sized business may assume that it is less at risk for ransomware attacks than a large corporation. China’s new cyber defense plans come in the wake of its increasing skepticism of hacking and cyberattacks from foreign countries through foreign made hardware and software, according to a Reuters report. They offer comprehensive compliant security solutions, including identity and access management, vulnerability identification, data encryption, managed firewall service, managed security patching, malware detection, and disaster recovery as a service. Such systems will reasonably include on premises mobile application stores, mobile management technologies, email servers, file servers, andintranet web servers. Its most recent update is a world class cookie consent management tool that can be toggled to appear for website visitors from specific regions and countries, which also includes consent analytics and cookie audit trails to meet auditor requirements. These reports combine the last three years of available results for the 2021 2023 BCIT Outcomes Surveys of 2020 2022 graduates and for Degree 2018 2020 graduates. Collection and analysis ofinformation might enable Orvilia or other parties to craft a narrative about an employee based on their interactions with the system, which could lead to apower imbalance between Orvilia and the employee and loss of trust in the employer if the employee discovers unanticipated monitoring. Your employees are your first line of defense against cyber threats. The Lightweight Directory Access Protocol, or LDAP, is a directory accessprotocol. Build and Operate Cloud Native Apps. Enterprise Security Solutions. Conduct a risk assessment, including thelikelihood and magnitude of harm, from:1. Pricing: Amazon Cognito Free for first 50000 MAUs, Next 50000 at $0. Which hardware based firewall solution do you recommend in 2022.

Now That It’s a Reality, Does Taiwan Still Back Extended Military Conscription?
Select Accept to consent or Reject to decline non essential cookies for this use. Least privileged accessis enforced for TLSserver private keys or,where possible,hardware securitymodules are used togenerate, store, andprotect TLS serverprivate keys. IPS – Intrusion Prevention System: A network security technology and control system that monitors networks and traffic for any vulnerability exploits or malicious activity which will automatically either allow or deny the detected traffic good or bad based on its established ruleset. These firewalls run on the Junos operating system and are available in physical, virtual, and containerized form factors. This begins with a complete threat intelligence report that is written up for all prospective clients. Sign up for a free trial today. This technology works with face recognition software built using FacePhi’s robust algorithms. It was very satisfying. SailPoint’s identity security platform helps businesses answer three main questions: Who has access to what. So don’t hesitate to employ this technology at your premise. Book Description Condition: New. As security practitioners develop new ways to keep cyber threats at bay, so malware authors continue to update their software and evolve their techniques to take advantage of new technologies and bypass security measures. Head of Security Services Analysis. This principle does not address system functionality and usability, but does involve security related criteria that may affect availability. Best for compliance and risk management. None of the face recognition app developers has denied the fact that these apps may use your pictures for commercial use. Conversely, if a company is paying for coverage that applies to outdated or irrelevant risks, it may be possible to abandon that coverage without creating a liability. Return to footnote 71. We’ll review several broad categories of cyber security solutions. OneTrust stands out as an industry leader. 2023 Comcast Business Cybersecurity Threat Report. Data compliance processes help organizations ensure that protected information is properly organized, managed, and handled according to the relevant regulatory requirements. Led by CENSIS Business Development Director, Cade Wells, this session explore cyber security exporting – including products, services and expertise. Develops a comprehensive strategy to manage:1. August 2012, and Deibert, Ronald J. Artificial intelligence can be used to super charge malicious cyber operations by enabling the rapid scanning of devices for vulnerabilities, the creation of targeted phishing lures and better malware, and the assessment of massive data sets for valuable information. Attending conferences and connecting with fellow professionals isn’t just about making connections, although that’s a big part of it. Drata’s platform integrates with and scans applications, so teams can shift energies toward other tasks. Intellectually, Artificial Intelligence: A ModernApproach provides both a conceptual artificial intelligence gym and arunning track to limber up on. Examples of ministerial directions include the Standing Directionsopens in a new window and ministerial statements of expectations.

SOC 2 Type 2 Report
Working with AIG’s claims experts and partners, it was quickly determined that infected files could be restored from system backups and no ransom payment was required. The administration of mobile devices such as smartphones, tablets, computers, laptops, and desktop computers. This is also a process that could potentially motivate secondary uses of personal information that are unreasonable. The DI example implementation shall identify and protect assets against malware that encrypts files and displays notice demanding payment. Com, we care deeply about your online security. Organizations are required to comply with various laws and regulations in order to operate in particular jurisdictions or across various jurisdictions. Pricing: Netgear products are priced between $40 to $300. We offer an easy to use, super scalable and highly available Cloud services which are self service. To sum up, Bitdefender BOX, Cisco ASA, CUJO AI, Fortinet FortiGate, NetGear ProSAFE, Palo Alto PA 7000, Netgate pfSense Appliances, SonicWall, Sophos XG, and WatchGuard Firebox are the top ten firewall hardware devices in 2022. DS 8—Integrity checkingmechanisms are usedto verify hardwareintegrity. Damage to or loss of informationsystems or networks. OM ADM 001SystemAdministrator. Find more information on Nation State adversaries and related resources. These threats remain resident on network infrastructure for long periods. Key Features: FortiGate comes with the following core features. We do not recommend this program to past participants of Cybersecurity for Managers: A Playbook unless you are looking for a refresher. To ensure unified management and consistent security policy enforcement, the firewalls are managed by Juniper Security Director Cloud. Best for Two Factor Authentication, Secure Logins. Already have a Full Immersion membership.

Enzuzo For
Head of Security Services Analysis. Your journey on the road to the application of datascience should start here. Elexo is a VAR expert supplier that distributes high tech electronic equipment such as computers and telecommunications for national security programs, including: – Rugged tablets and rugged PDAs – Rugged laptops – Networks and telecoms – Forensic and security – Radio frequency and microwave. More Protection – software is designed to prevent, detect, and help remove threats from computer systems in an efficient manner. DevOps – a portmanteau of “Development” and “Operations”: A set of practices combining both development and operations. Find out more about the Kindle Personal Document Service. This makes them more vulnerable to hacking and means confidential devices and information will have to be used for protection. If you don’t host financial data, this is the only compliance audit you should complete. Using access control lists oridentity management systems. With that in mind, you also need to establish accountability. Passwordless authentication enables organizations to replace passwords with other forms of authentication, such as password generators, biometric signatures, and tokens. Applicants who have completed post secondary studies outside of Canada, the United States, the United Kingdom, Australia or New Zealand will require a comprehensive evaluation of their credentials by the International Credential Evaluation Service ICES. TranThe Civilian Cyber Incident Response Policies of the U. Editorial comments: Users frequently switching between personal and professional use on the same device should consider CUJO, as it lets you set up different security profiles for different use cases. With the company’s solutions, organizations can monitor for threats, locate weaknesses and act quickly when viruses strike. Other features of the platform include one click remediation and reduced security review times. Rather than taking our word for it, it is worth reading the specific details of your policy to properly understand what you are and aren’t covered for. Performing a selective wipe is an option that only removes enterprisedata from the device instead of being a full factory reset. Next Generation firewalls NGFW or NextGen firewalls are a little different to the other firewalls in this list. It should also be able to scan behind the logins and find any business logic errors.

The Importance of TikTok Advertising
Additionally, privacy enhancing technologies typically leverage privacy aware machine learning ML algorithms to decentralize data processing and analytics. For a start, the framework states that compliant organisations can only share data with other organisations that have passed the audit. Table 6‑5 Test Case ID: Data Integrity IP 3. Enterprise cybersecurity can seem like a complex puzzle. Windows 11 Forum is dedicated to helping you find support and solutions for any problems with your Windows 11 PC, we also provide an extensive Windows 11 tutorial section that covers a wide range of tips and tricks. Cybereason offers a unified cybersecurity platform that combines endpoint prevention, detection, and response in a single lightweight agent. Additionally, Gartner has identified three key factors that are fueling this growth: an increase in remote and hybrid work; a transition from Virtual Private Networks VPNs to zero trust network access; and a shift to cloud based delivery models. For example, it uses multiple methods of analysis to detect unknown threats, including static analysis with machine learning, dynamic analysis and bare metal analysis. Security breach fees can also include the costs of hiring an IT professional, a forensic accountant, or other professional services. In addition, companies must also adhere to various privacy acts. Recommended: Guide to compliance risk. Such projections are obviously an inexact science. Cybercriminals don’t attack small businesses. Here are some of the ways that you can take to boost your organization’s overall cybersecurity stance. Perform cyber defense trend analysis and reporting.
Guide to Cybersecurity Law Society of Scotland
The reports are organized into three page summaries containing information on graduates’ labour market experiences and opinions regarding their education. He ends up joining a misfit team: The Leader, Armitage ex military; The Assassin, Molly a beautiful cyborg; The Techie, Finn a prototypical scrounger; and The Mentalist, Peter a psychopathic mind bender. Timeero also lets users set up geofences or special device codes in order to determine employee location while punching in. Providing comprehensive network security solutions for the enterprise, large business and SOHO, Netgate solutions with pfSense Plus software bring together the most advanced technology available to make protecting your network easier than ever before. VSphere vSAN NSX Aria. By acquainting yourself with compliance demands and maintaining your documents and reports in order may expedite the process and assist your auditor in quickly locating the required information. OV PMA 005 IT ProgramAuditor. 400 NW 26th St, FL 33127, Miami. Leaders from across the Canadian privacy field deliver insights, discuss trends, offer predictions and share best practices. AUDIT EVENTSControl: Verify that the system can audit thefollowing event types:. Sales Professional Business Development Database AI Cybersecurity Telecommunications Web 3 Blockchain Queensland Based. Learn how you can get your SOC 2 faster by requesting a demo. The latter only applies to a SOC 2 Type II audit, described in more detail in the next section. ” The phrase “compromises the security or privacy of the protected health information” was defined to mean “poses a significant risk of financial, reputational, or other harm to the individual. These companies provide network security solutions including firewalls, intrusion prevention systems, endpoint security, and cloud security. Its comprehensive vulnerability and malware detection make speedy remediation possible for any malware or vulnerabilities found. At Morgan Stanley, safeguarding your assets and personal information is a top priority, but you have a vital role to play. 5%, accounting for 18. De identification techniques may be applied to aggregated databefore sharing it with third party analytics and publicly. Connect with him on LinkedIn, follow his updates on Twitter, or explore more about him on his personal website. An important consideration in thinking about China’s cyber operations is that, to date at least, China has been constrained in its actions by its desire to be a respected member and eventually leader of the global community. It is Cisco’s largest and longest running Cisco Corporate Social Responsibility program. Please provide a Corporate Email Address. © University of Maryland Francis King Carey School of Law. Certificates arereplaced duringoff hours and aretested before goingoperational. Also known as the Budapest Convention, this document is the only binding international instrument designed specifically to combat cybercrime. 3 PasswordManagement System. Endpoint Protection Cloud Device Starts at $2. Certified CSA STAR Auditor.
Cyberattacks and attackers’ tools
Responders can gather comprehensive data and analyze it quickly via pre built dashboards and easy search capabilities for both live and historical artifacts. Today, cyber security teams are often overwhelmed while trying to manage these complex cyber security architectures. Modern application development methods—such as DevOps and DevSecOps—build security and security testing into the development process. This is much more cost effective in comparison to dealing with a data breach or theft which can costly in terms of recovery of money lost and sensitive data acquired by malicious attackers. Ensure that the system and communicationsprotection procedures implement the system andcommunications protection policy and controls; ande. They exploit never before seen cyber weaknesses – so called zero day vulnerabilities. Cloud web security has several challenges associated with it. This article will detail SOC 2 compliance and provide a checklist of actions you can take to achieve and maintain adherence. As an enterprise level privacy platform, Usercentrics has dedicated tools that obtain, manage, and document user consent, and it leverages tools for consent storage and consent APIs. Second, as shown by the U. 2Information RiskAssessmentProcess. They should adopt a Zero Trust security framework to protect networks, implement stringent identity and access management controls, and secure virtual private networks VPNs and encryption. We go in depth to all five below but only security is required for SOC 2. For each category, it defines a number of subcategories of cybersecurity outcomes and security controls, with 108 subcategories in all. National Institute of Standards and Technology NIST, “NIST Privacy Engineering Program,”. If you are interested in contributing, please reach out to intl cyber privacy nist.
SecuritySecure Apps and Clouds
The compliance management system comprises all measures, structures and processes that a company or an organisation establishes to ensure compliance with the rules and law. The kind of job you do is definitely something you wish to consider before you step foot in any field. But primarilyI was impressed with the presentation of the bits I read,especially the focus on agents and environment, elements ofdecision making and so on. Meanwhile, other vendors that had gotten their start in SD WAN such as Cato Networks have now become major players in SASE as well. Key Features: Netgear ProSAFE has the following key functionalities. Rapid7 specializes in cybersecurity and data analytics, offering vulnerability management, application security, IT operations, penetration testing, security information and event management SIEM, managed services and security advisory services. Return to footnote 51. The firewall inspects this header information to let in only legitimate traffic. Furthermore, the development of a positive Internet culture is designed to improve online protection for minors. Identity and access management IAM solutions help organizations identify and manage who has appropriate access across their hybrid multi cloud environment. The goal of the plan is to contain “major risks” to threats to the industrial sector by the end of 2026 with the implementation of protective measures that will be applied to more than 45,000 companies in that vertical. A cloud security company offers security tools that are designed for the cloud, and to work across multi cloud environments. Location: Broomfield, Colorado. It should be comprehensive, covering all the operational aspects of the project and the measurement instrument to be employed. Fortinet has a wide range of cloud security offerings. Offers a comprehensive range of cybersecurity solutions for businesses. Certified Ethical Hacker. Anti Money Laundering Software. Cybersecurity Framework Steps for Small Manufacturers helps small manufacturers understand the NIST Cybersecurity Framework and how it can be used to manage their cyber risks. International Cyber Security Protection Alliance May 2013. The key regulatory challenges of 2024 include both new legislation and strong supervisory frameworks for existing guidance, according to a new KPMG report. Find out more about saving content to Google Drive. Traditional appliance based solutions are less effective in the face of these modern challenges, making the NSX Distributed Firewall a valuable option for addressing internal network security needs. Only the URLs that aren’t in this database can pass through.
SOCIAL NETWORKS
This is an important development and shows just how critical it is to have a state of the art workforce able to thwart nation state actors who may attempt to harm our democracy. While the original phishing scams were relatively easy to detect, modern attacks are convincing and sophisticated to the point where they can be virtually indistinguishable from legitimate emails. A photo is pretty straightforward. They work at the session layer in the OSI model. Learn more in our Cookie Policy. “My CFC lead talks a lot about SOC life,'” he says. Cybersecurity product categories: Risk management, web security, cloud security. The electronic systems and digital networks that facilitate these transactions and communications also capture our preferences and other personal details, and track our online and, increasingly, physical movements. See, for example, Symantec “New Survey Shows U. This course will be focusing on building a foundation that leads to FSCT8621, Graduation Project 2. Available: egacy/IR/nistir7711. Overall, it provides the necessary visibility to prevent cyberattacks, insider attacks, and more. Identify the purpose of the risk assessment in terms of the information that the assessment is intended to produce and the decisions the assessment is intendedto support. For instance, FaceApp – the famous face recognition app that went viral earlier this year and which we have discussed above as well – has been designed by a Russian based firm. At worst, it’s bad risk hygiene for your data and your IP. Bonus: Cybereason has a podcast channel like some of the other security vendors. Agree and Join LinkedIn. TrendMicro’s cybersecurity solutions are designed to provide protection against advanced cyber threats. Well, in this article, you’ll learn about the fascinating techniques that help investigators unravel online crimes and protect our privacy. The company’s Mobile Endpoint Security uses AI to safeguard smartphones, tablets and Chromebooks, while Zero Trust Network Access gives organizations the ability to let employees access work related apps without putting company data at risk. Reverse Image Search by Photo. “Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to meet its objectives.